Email: info@fc-llc.org
by Freedom Consulting Posted on June 19, 2020

Quick Security Checklist for Remote Workers
With the advancement in technology and its’ availability, working remotely has been a growing option for businesses around the world. Due to the COVID-19 pandemic, more companies have gone to remote-based workstations than ever before. An article in Vox discusses the rise in the public company transcripts from Sentieo that mention working from home. (Molla, 2020)
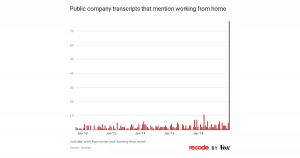
As you can see, there is a dynamic rise in work at home mentions in February and March, due to government lockdowns. With the increase of remote workforces, there has been an increase in cyber-attacks. According to ITC Secure, since the beginning of 2020, and the COVID-19 pandemic, the number of cyber-attacks has increased dramatically. (Itc, 2020)
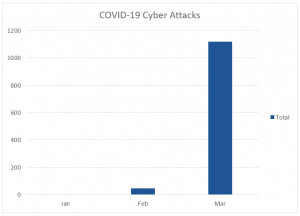
As we get closer to going back to work after the pandemic, more and more companies are weighing the option of letting their employees continue to work from home permanently.
We will focus on some simple steps that individual remote employees should take to safeguard their company’s data (not to mention their personal data). While these security measures are important for everyone, they are especially crucial for companies with employees working remotely, whether from home or while traveling. While there are security risks associated with remote workstations, there are steps that can be taken to help mitigate possible threats. Even though ensuring that company data is secure and protected is the primary responsibility of the Chief Security Officer (CSO or CISO), it falls on everyone to do their part. This means employees taking appropriate steps to secure their devices and home networks, and companies providing the proper resources to facilitate their employees. Today’s reality is that not all employees can come to the structured building and controlled environment.
Security measures are just one thing to consider when setting up your remote workstations. Companies should look for ways to allow for location flexibility while also keeping data safe. If your devices are online, you are at risk.
• Use supported versions of your device’s operating system. Security vulnerabilities are discovered frequently and can affect not only the newer versions, but any version, supported or not. Developers generally do not support the outdated versions leaving vulnerabilities that require a security patch.
• Keep the operating system up to date. On average, companies take about 197 days to identify and 69 days to contain a breach according to IBM. (source: https://www.varonis.com/blog/data-breach-response-times/). To get security patches as quickly as possible, ensure your device has automatic updates turned on and that you frequently apply them. Side note: By default, automatic updates are enabled on most modern devices.
• Keep your software up to date. It is essential to keep your applications up to date. Devices will give you the option to allow for automatic software checks and updates; or have it prompt the user to manually update. For everything else, make sure to check that you are using the latest version periodically.
• Encrypt your devices. Encryption helps prevent unauthorized access to the data on your devices. It can be especially important in case of a lost or stolen device, as it helps prevent anyone from accessing your data without your password or pin.
• Disable automatic login from unattended devices while not in use. Users should ensure that automatic login is disabled, and that a password, pin, or a biometric alternative is required when turning them on or resuming from sleep. Automatic login is disabled by default on most modern devices.
• Enable automatic locking on devices. Users should lock devices when stepping away from coworking spaces or remote working locations. Configure an amount of time that is not unreasonably long, but ensures unattended devices are not open targets, such as 30 seconds for mobile devices or 5 minutes for laptops.
• Use a complex pin/password on your devices. This is generally the first line of defense. If this is easily penetrated, the additional steps taken are irrelevant. Avoid anything easy to guess or related to you. A strong pin/password should look random to anyone that is not you.
• Use a password manager. To keep your data safe, all your passwords and pins should be unique, appropriately difficult, and be reset periodically. Managing this can be extremely cumbersome. Password managers handle all of this for you. They help you create strong passwords and remember them. Password managers automate and simplify a lot of the tedious work associated with password hygiene.
• Enable two-factor authentication & use an authenticator application. Two-factor authentication means using two different factors to verify your identity to an app or site. The first, and most common, is your password. The second can take many forms but is typically a one-time code. Having two-factor authentication enabled reduces the chances of fraud, data loss, or identity theft.
• Enable “Find my device” and remote wipe. If a device is lost or stolen, being able to locate and wipe devices remotely can be crucial. “Wiping” makes it much harder to access your data, no matter how much time or determination an attacker has.
• Remove all your information from any device you dispose of or recycle. When lending, giving, selling, or trashing a device, it is important to wipe it and reset it to factory settings. This prevents your data from being accessed after you no longer have control over your device, temporarily or permanently.
• Use a Virtual Private Network (VPN) on public or untrusted networks. A VPN establishes a secure and encrypted connection to another network over the Internet and routes your traffic through it. This substantially improves your online privacy and anonymity. Be sure to research the different VPNs offered to determine the best one to fit your needs.
• Use your best judgment. Online security or privacy does not boil down to a fixed set of guidelines. Being protected can be situational, and you often need to use your best judgment.
• Do not click on links that look suspicious or are from unknown senders. Phishing campaigns are among the most popular ways to conduct attacks today. If you are sent a suspicious-looking link, confirm with the sender if they are known. Make sure that you report and suspicious links to the appropriate person(s) within the company. (Silva, Gonçalo, 2020)
We have entered an ever-changing climate that we are all adapting to. These are just some easy steps that you can take to start to secure yourself while working remotely. Being vigilant, aware, and taking precautions can help you mitigate threats and vulnerabilities against your company and your personal networks. Remember, security is everyone’s responsibility.
WR-Freedom Consulting LLC
© 2024 Freedom Consulting LLC. All rights reserved